Here you can find a post by Andreas Peetz that explains how to avoid users to ‘safely remove devices’ in virtual machines.
Various ways to address the "Safely Remove Hardware" Tray Icon issue
by Andreas Peetz at Sunday, February 23, 2014
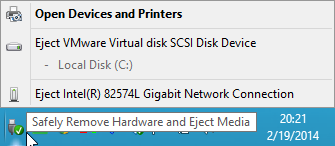
Since a long time VMware supports device hot plug in its Virtual Machines. This leads to the "Safely Remove Hardware and Eject Media" tray icon to be displayed in Windows VMs, and it allows a user to eject the network card and even hard disks from the machine. While the latter will fail in most cases, because the hard disk is in use by Windows, ejecting the NIC will succeed ... and it will do exactly this. The NIC will disappear from the VM, which will disconnect from the network until a VMware administrator re-adds a new NIC to it!
How many times were curious Windows Admins or VDI desktop users not only tempted by this possibility, but even used it - only to find themselves disconnected from their machines with no way to re-connect ;-) ?! The first few times this may be funny, but then you will want to look for ways to prevent this.
Google is you friend, and you will easily find many different ways to address this issue, but scattered across even more blogs and sites. This is my attempt to collect all of them in one blog post.
1. Disabling Hotplug in VM properties
This method is recommended by VMware and described in there KB1012225. Just add the configuration parameter
devices.hotplug = "false"
to the VM and this will prevent virtual NICs and SCSI controllers to appear as removable devices. This blog post nicely describes how to do this via PowerCLI.
Of course the VM needs to be powered off to do this change. This can become tedious if you have a lot of VMs, and what if you do not even have administrative access to the VMware environment, because you are just a user of it?
Well, there are also several ways to address the issue from within the Guest OS ...
2. Hide the Notification Area through GPO
Windows offers many options to customize the user experience and restrict desktop GUI options through Group Policies (AD Domain based or local). Unfortunately there is no setting to disable just the "Safely Remove Hardware" tray icon, but you can hide the complete notification area (aka "system tray") of the taskbar:
Hide the notification area through Group Policy
You will find the setting in the folder "User Configuration \ Policies \ Administrative Templates \ Start Menu and Taskbar" of the Group Policy Management Editor.
However, it will hide all tray icons of all applications. So this might not be suitable for every environment.
3. Hide only the Safely Remove Hardware Tray Icon by Utility or Reg-Script
If you do not want to hide the complete notification area, but only the "Safely Remove Hardware" icon then you can use a handy little free tool called Icon Remover for this. It has a GUI for interactive use, but can also be called from a command line with parameters /hideicon (and /showicon for the reverse effect) to do the job. So you can just call it from a mandatory logon script to run it automatically for each user that logs on to the console or via a Remote Desktop session.
A guy named Raymond found out that this tool does nothing more than changing a registry value (namely HKCU\Software\Microsoft\Windows\CurrentVersion\Applets\SysTray\Services) and calling systray.exe after that to refresh the system tray display. And he provided an easy cmd script that does the same:
1reg add "HKCU\Software\Microsoft\Windows\CurrentVersion\Applets\SysTray" /v "Services" /t reg_dword /d 29 /f
2systray
No matter if you use the Icon Remover tool or this script: You may run into timing problems when using this approach to hide the icon. It looks like the registry value is reset to its original value (decimal 31) when the user logs off and on again, and the tool or script must run after the Explorer desktop view including the system tray has fully initialized and is displayed on the screen. This is also the reason why you cannot just set this registry key through a Group Policy - these are applied before that during the logon process.
4. Disable Hotplug for particular devices through registry
Finally you may run into a situation where you really do not want to remove the "Safely Remove Hardware" icon, but only the VMware SCSI and NIC devices from it. Virtual desktops that are accessed through VMware View or Citrix XenDesktop offer a way to redirect local USB devices into the VM and these also appear as removable devices. If you removed the tray icon the user would also not be able to disconnect such devices from the VM. So, how do you prevent just the VMware SCSI controllers and NICs from appearing as removable devices?
Helge Klein explains on his blog how to do this: In the Windows registry you can change the capabilities of the virtual PCI devices to not include the Removable bit. He mentions the command
reg.exe add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\PCI\VEN_8086&DEV_100F&SUBSYS_075015AD&REV_01\4&3ad87e0a&0&0088" /v Capabilities /t REG_DWORD /d 2 /f
to delete the flag for a virtual e1000 NIC. But be aware: The last part of the key path (here: 4&3ad87e0a&0&0088) depends on the Windows version that you are using (and maybe other things), so you can not rely on the same path being valid for all your Windows VMs! In the comments of Helge's post you will find a Powershell script that takes this into account and searches for the correct path of a vmxnet3 adapter. You can run such a script in a policy triggered Computer startup script to make the required changes.
To make the script work for other types of adapters you need to change the PCI ID at its beginning. For your reference here are the PCI identifiers (as listed in the registry) for some of the SCSI controllers and NICs that you can configure for VMs (I determined them using a Windows 8 VM):
SCSI Controllers:
- LSI Logic Parallel:
VEN_1000&DEV_0030&SUBSYS_00000000&REV_01 - LSI Logic SAS:
VEN_1000&DEV_0054&SUBSYS_00000000&REV_01 - PVSCSI:
VEN_15AD&DEV_07C0&SUBSYS_07C015AD&REV_02
- e1000:
VEN_8086&DEV_100F&SUBSYS_075015AD&REV_01 - e1000e:
VEN_8086&DEV_10D3&SUBSYS_07D015AD&REV_00 - vmxnet3:
VEN_15AD&DEV_07B0&SUBSYS_07B015AD&REV_01
After all it's quite cumbersome to address the issue from within the Guest OS, and - like VMware - I would definitely recommend to use option #1 instead and edit the VM's properties to include devices.hotplug = "false" whenever you can.
However, you should be aware that this method does not only prevent ejecting devices from the VM, it will also prevent hot adding them. So you also won't be able to add a new NIC, SCSI controller or USB adapter to the VM while it is powered on. Hot adding hard disks to existing SCSI controllers will work though. And hot adding CPUs and RAM also works independently from the PCI hot plug functionality and will not be interfered by disabling the latter.
This post first appeared on the VMware Front Experience Blog and was written by Andreas Peetz. ![]() Follow him on Twitter to keep up to date with what he posts.
Follow him on Twitter to keep up to date with what he posts.

No comments:
Post a Comment